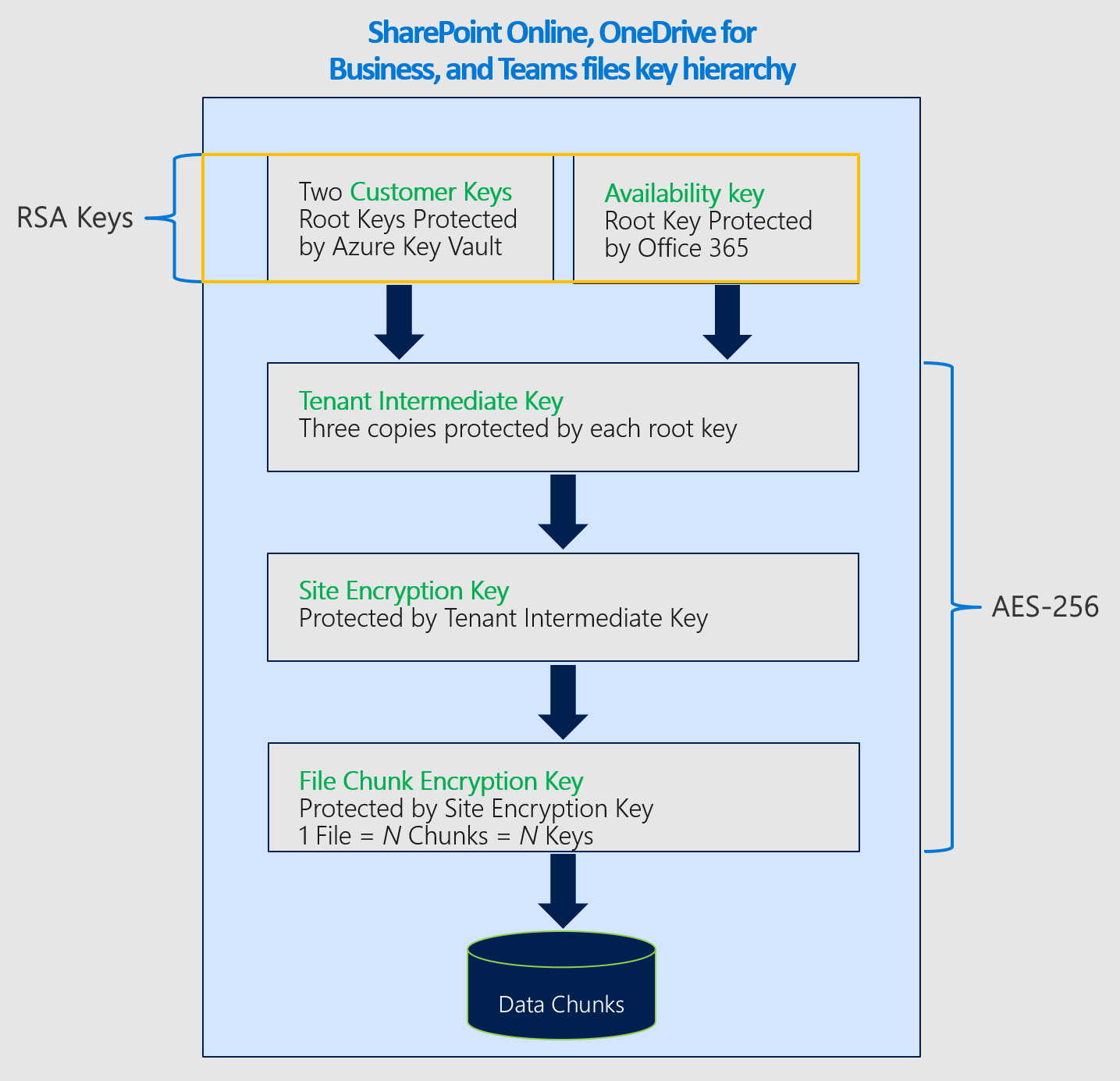
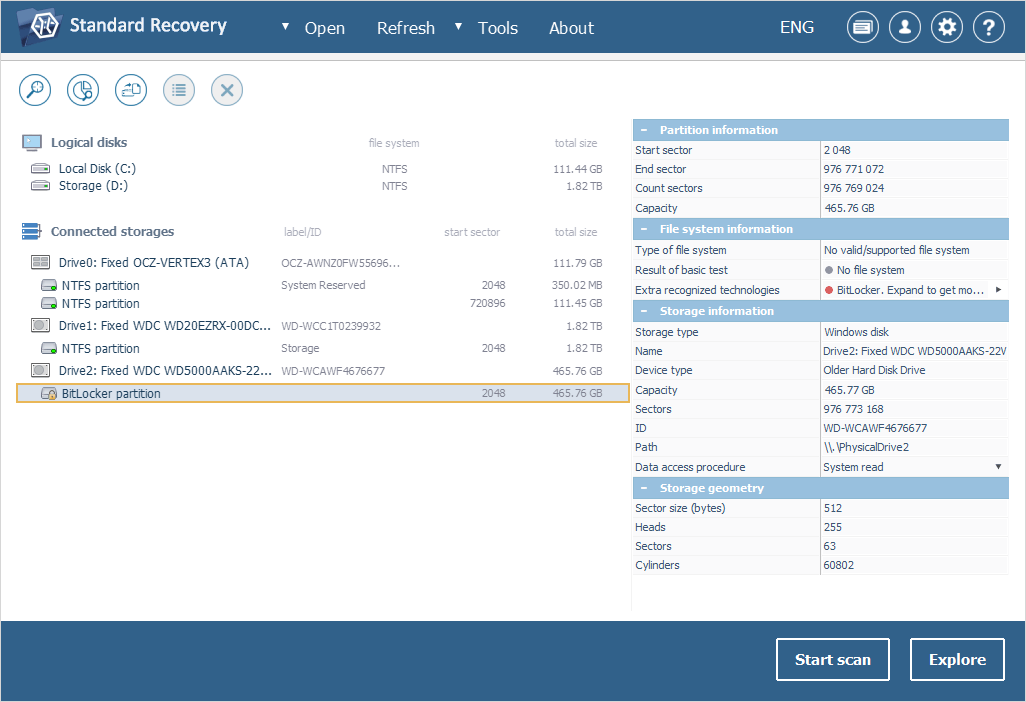
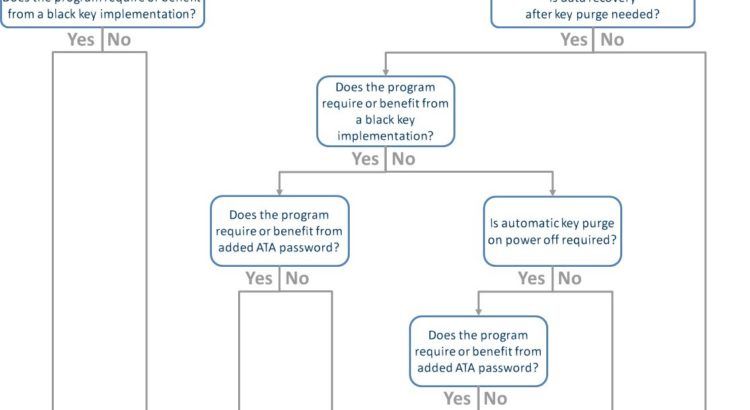
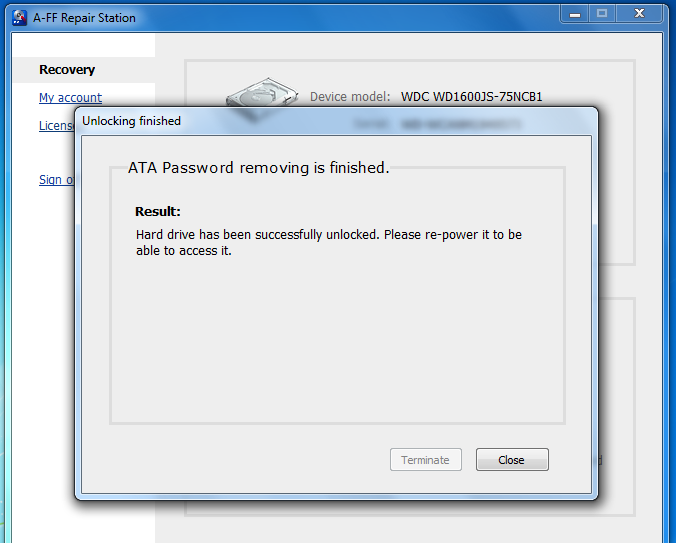
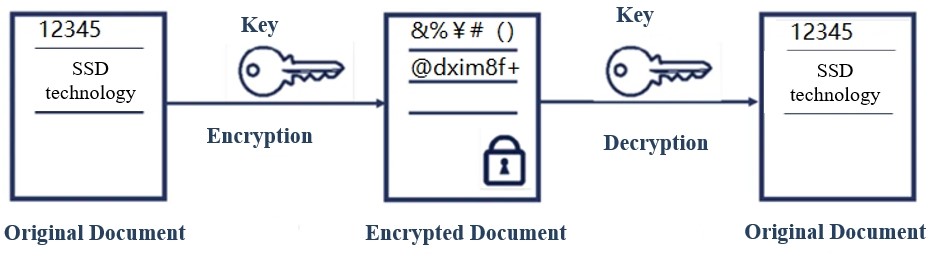
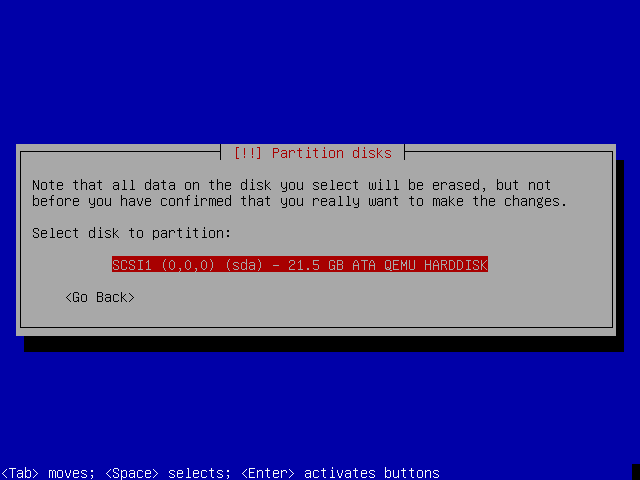
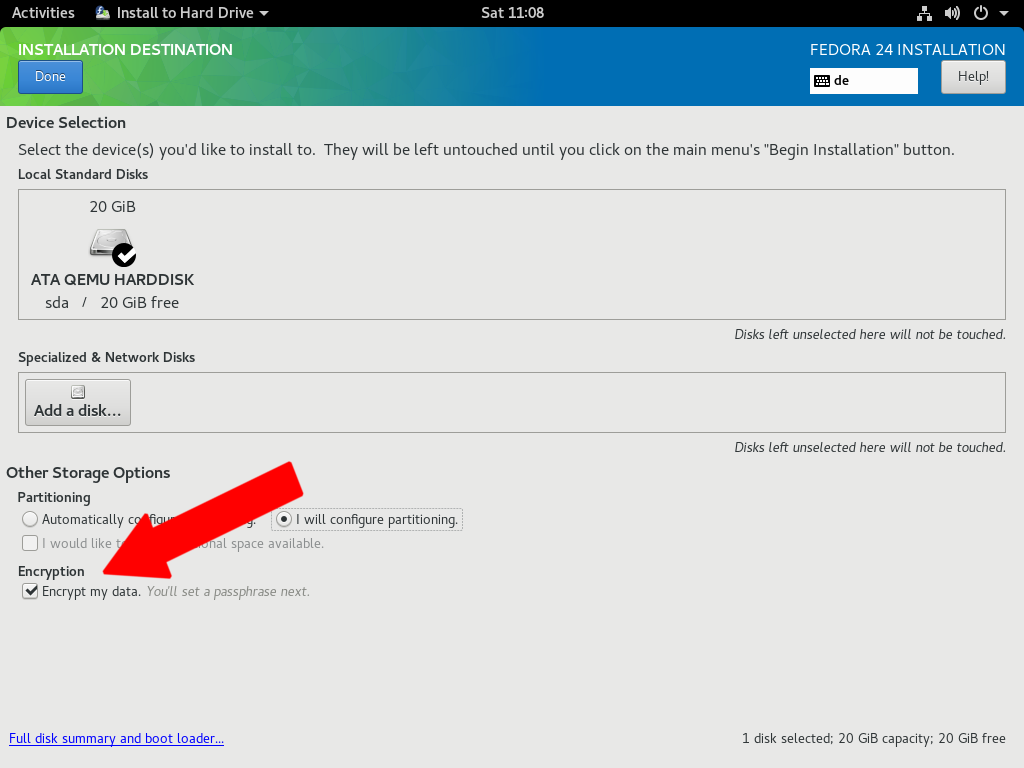
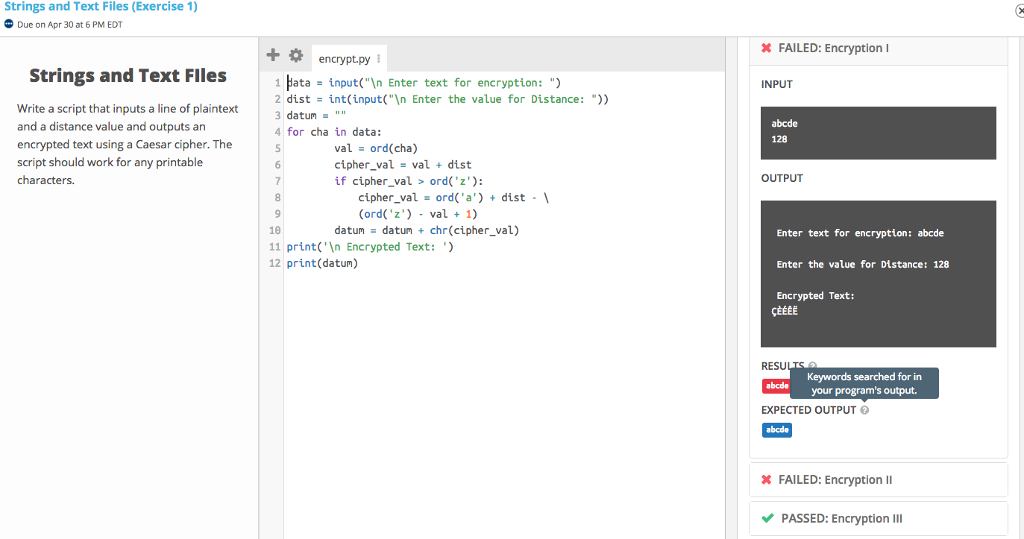
The frame work of the portable hard disk encryption/decryption system... | Download Scientific Diagram

Lab of a Penetration Tester: Week of Evading Microsoft ATA - Day 2 - Overpass-the-hash and Golden Ticket
![Cisco ATA 191 and ATA 192 Analog Telephone Adapter Provisioning Guide for Multiplatform Firmware - Deployment and Provisioning [Cisco ATA 190 Series Analog Telephone Adapters] - Cisco Cisco ATA 191 and ATA 192 Analog Telephone Adapter Provisioning Guide for Multiplatform Firmware - Deployment and Provisioning [Cisco ATA 190 Series Analog Telephone Adapters] - Cisco](https://www.cisco.com/c/dam/en/us/td/i/300001-400000/390001-400000/393001-394000/393514.eps/_jcr_content/renditions/393514.jpg)
Cisco ATA 191 and ATA 192 Analog Telephone Adapter Provisioning Guide for Multiplatform Firmware - Deployment and Provisioning [Cisco ATA 190 Series Analog Telephone Adapters] - Cisco